Here we use the tool "Cain and Abel" for cracking passwords of any local user/administrator.
Make sure that you have disabled the antivirus/firewall running on your system before installing and throughout this process.
Two most effective techniques used here are "Brute-Force" and "Cryptanalysis".
Brute-Force:- As this techniques takes more time to complete, the attacker prefer this technique only when there is a hope that the password contain same type of characters or may be two. i.e only loweralpha, only alpha, only numeric or may be loweralpha-numeric, also it should contain less than 7 characters. Otherwise it takes more time to crack password, which may be the mixture of all types of characters along with special symbols.
The step-by-step explaination for this technique is given below-
1) Open the tool "Cain and Abel"
Make sure that you have disabled the antivirus/firewall running on your system before installing and throughout this process.
Two most effective techniques used here are "Brute-Force" and "Cryptanalysis".
Brute-Force:- As this techniques takes more time to complete, the attacker prefer this technique only when there is a hope that the password contain same type of characters or may be two. i.e only loweralpha, only alpha, only numeric or may be loweralpha-numeric, also it should contain less than 7 characters. Otherwise it takes more time to crack password, which may be the mixture of all types of characters along with special symbols.
The step-by-step explaination for this technique is given below-
1) Open the tool "Cain and Abel"
2) Go into the category "Cracker" it displays all sub-categories under "Cracker" in left panel.
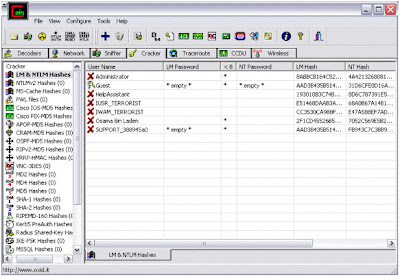
3) Select "LM & NTLM Hashes" from left panel and then click on + symbol, you will be greeted by a window as shown.
5) Right clicking on any username shows all available options using which we can crack it's password
5) Right clicking on any username shows all available options using which we can crack it's password
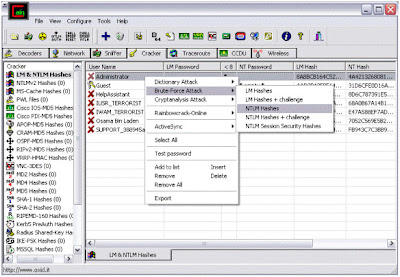
6) Here we select "Brute-Force Attack" and then "NTLM Hashes", since windows uses NTLM hashes to store local users' passwords.
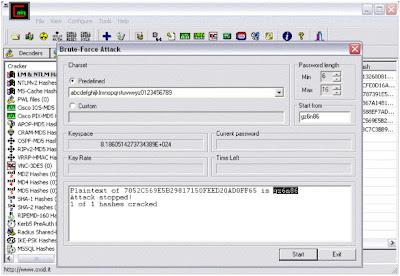
7) You will be greeted by a window where you can modify properties for brute-force attack such as password length, character set, etc.
7) You will be greeted by a window where you can modify properties for brute-force attack such as password length, character set, etc.
8) Click on "Start" button.
9) On completion it will reveal the exact password.
9) On completion it will reveal the exact password.
Cryptanalisys:- Basically, Cryptanalisys means Operations performed in converting encrypted messages to plain text without initial knowledge of the crypto-algorithm and/or key employed in the encryption.
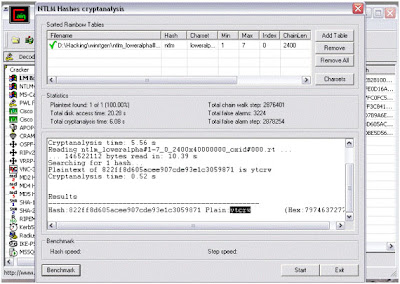
This is the fastest technique of password cracking possible due to "Rainbow Tables".
A rainbow table is a file that is used to lookup an unknown plaintext from a known hash for an algorithm that does not usually permit this operation.
Steps 1 to 4 i.e upto importing hashes from local system, are similar to previous technique (i.e brute-force). The steps coming after that are as follows-
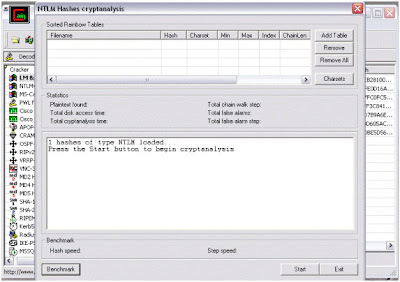
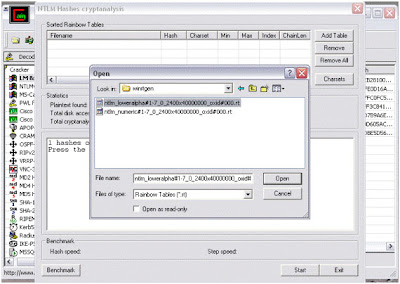
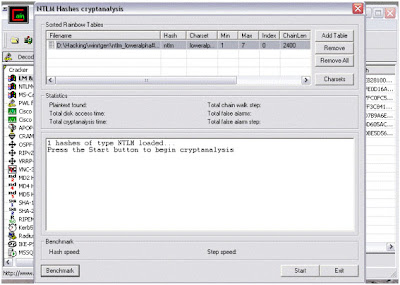
5) Here, select "cryptanalisys attack" then "NTLM hashes" and then select "via rainbow tables". Here we can choose either OphCrack or RainbowCrack formats of tables. The rainbow tables are available free to download on internet.
This is the fastest technique of password cracking possible due to "Rainbow Tables".
A rainbow table is a file that is used to lookup an unknown plaintext from a known hash for an algorithm that does not usually permit this operation.
Steps 1 to 4 i.e upto importing hashes from local system, are similar to previous technique (i.e brute-force). The steps coming after that are as follows-
5) Here, select "cryptanalisys attack" then "NTLM hashes" and then select "via rainbow tables". Here we can choose either OphCrack or RainbowCrack formats of tables. The rainbow tables are available free to download on internet.
7) Browse for the location of rainbow table on your system, select proper table and click "open".
To learn windows password cracking techniques properly, one must understand "LM" & "NTLM" algorithms, SAM File, Dumping NTLM hashes from local SAM, Rainbow Tables, etc.......!





1 comments:
Write commentshey nice post buddy..
ReplyKeep up the good work
EmoticonEmoticon